AWS WAF (Web Application Firewall) is a service that protects web applications from malicious attacks by filtering and monitoring incoming traffic based on defined rules. It safeguards against common web vulnerabilities such as SQL injection, cross-site scripting, and more.
Create AMI Template:
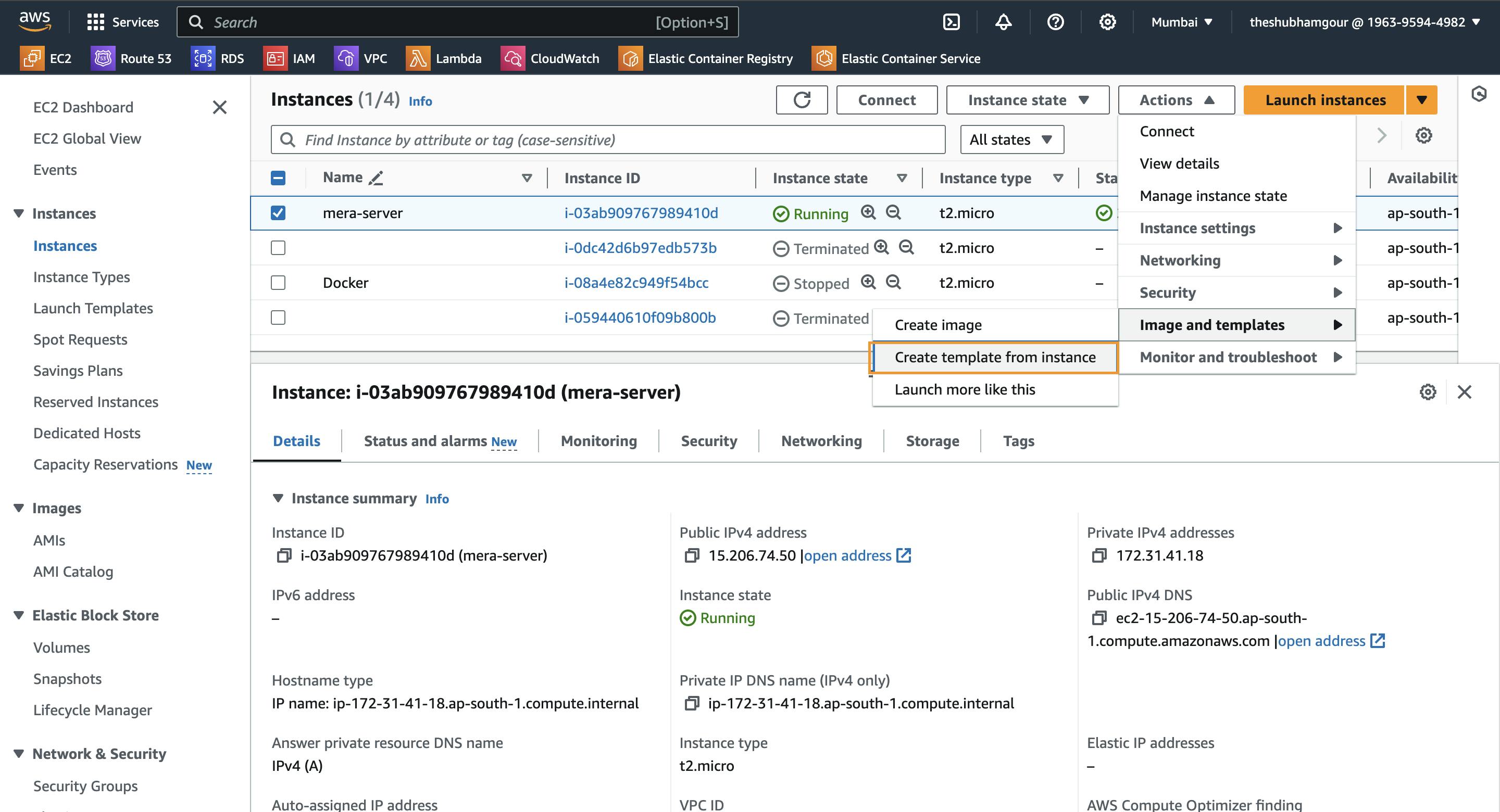
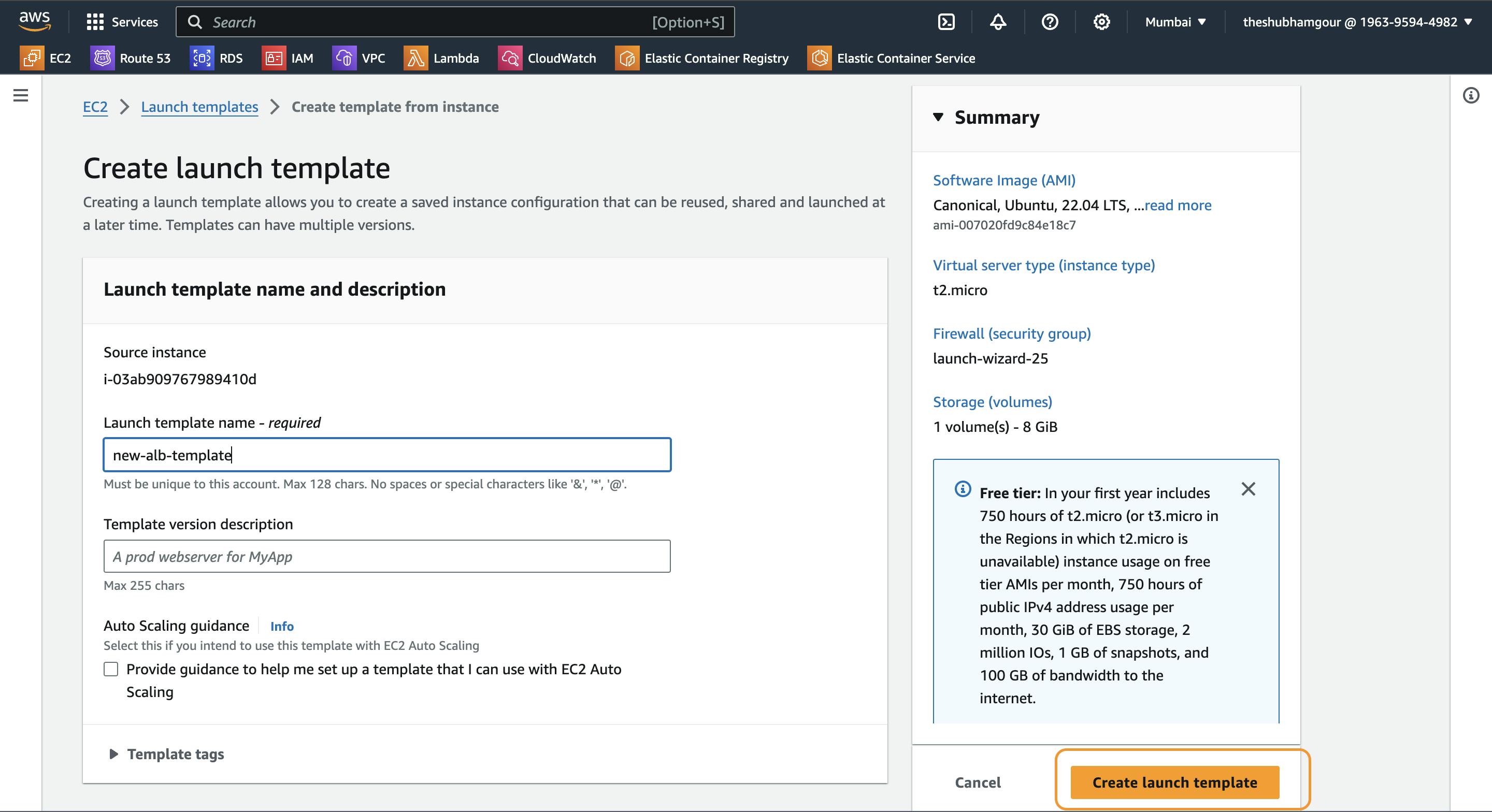
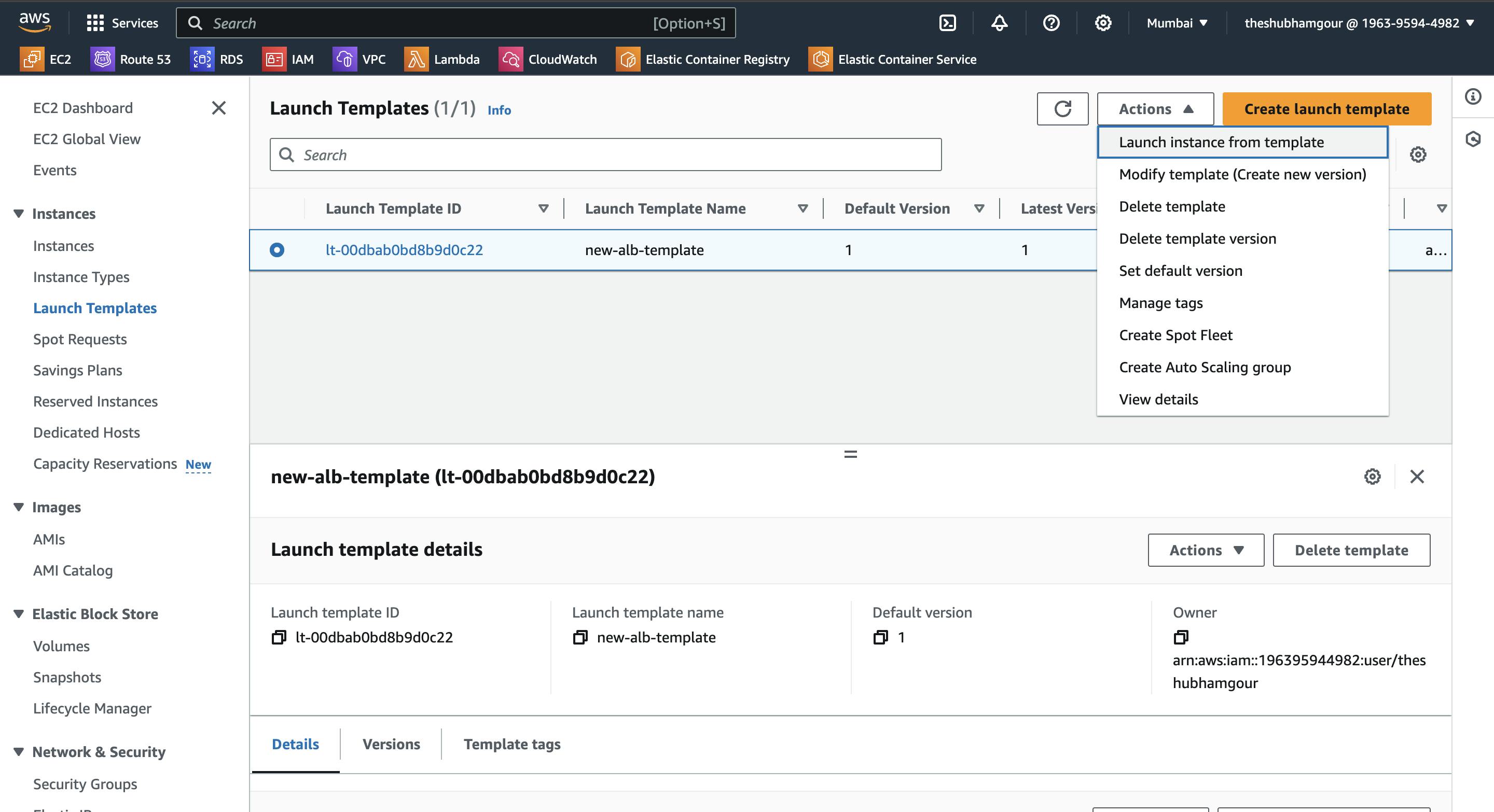
Now Launch instance from the template:
If you have a web application hosted on AWS, you can use AWS WAF to set rules that block requests from specific IP addresses or patterns commonly associated with attacks.
Implementing AWS WAF for Web Application Protection
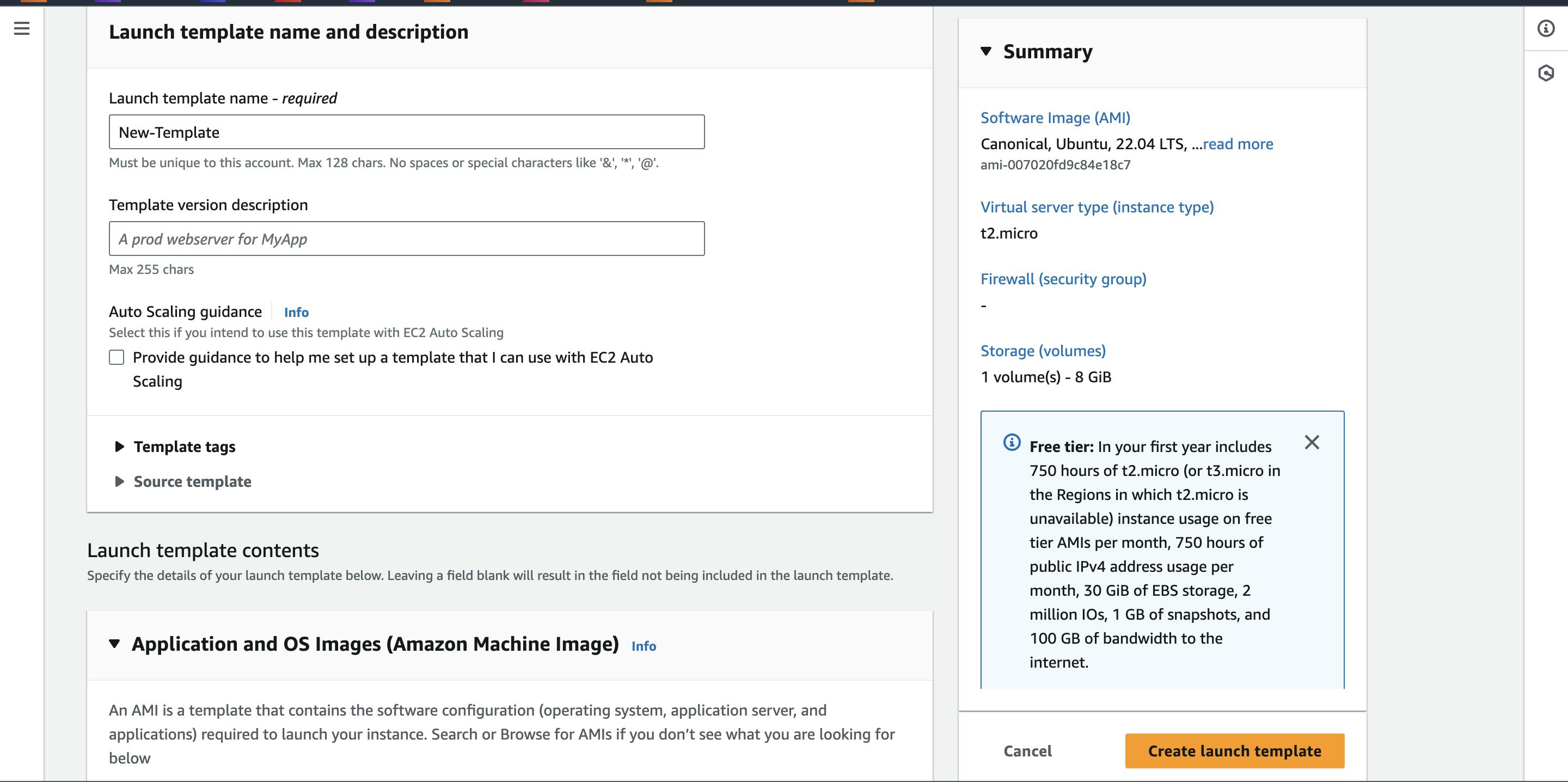
Navigate to the EC2 Dashboard and locate the "Launch Templates" section.
Click "Create Launch Template" and configure settings like AMI, instance type, and storage.
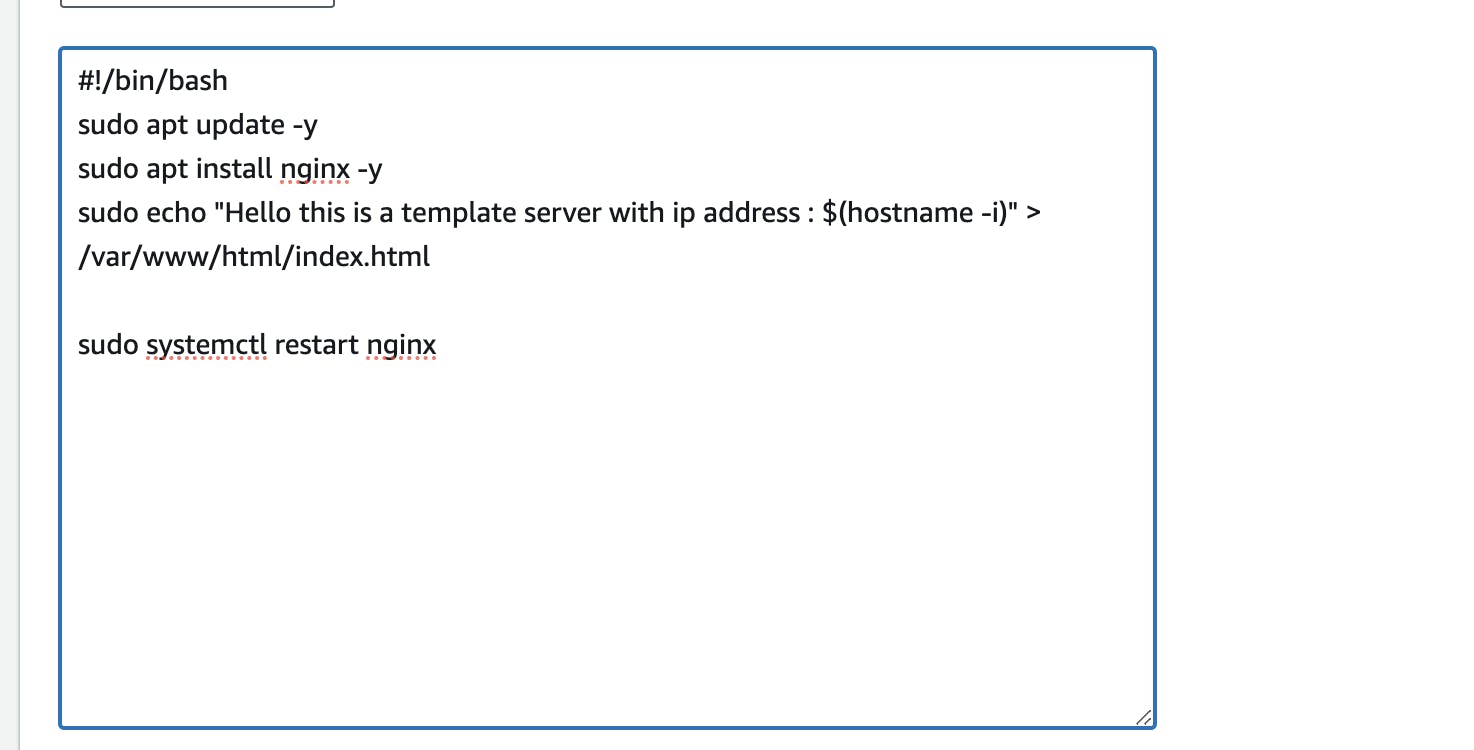
In the "Advanced Details" section, paste the provided script.
#!/bin/bash
sudo apt update -y
sudo apt install nginx -y
sudo echo "Hello this is a template server with ip address : $(hostname -i)" > /var/www/html/index.html
sudo systemctl restart nginx
Save the template.
Create Load Balancer
In the EC2 Dashboard, navigate to "Load Balancers" and click "Create Load Balancer."
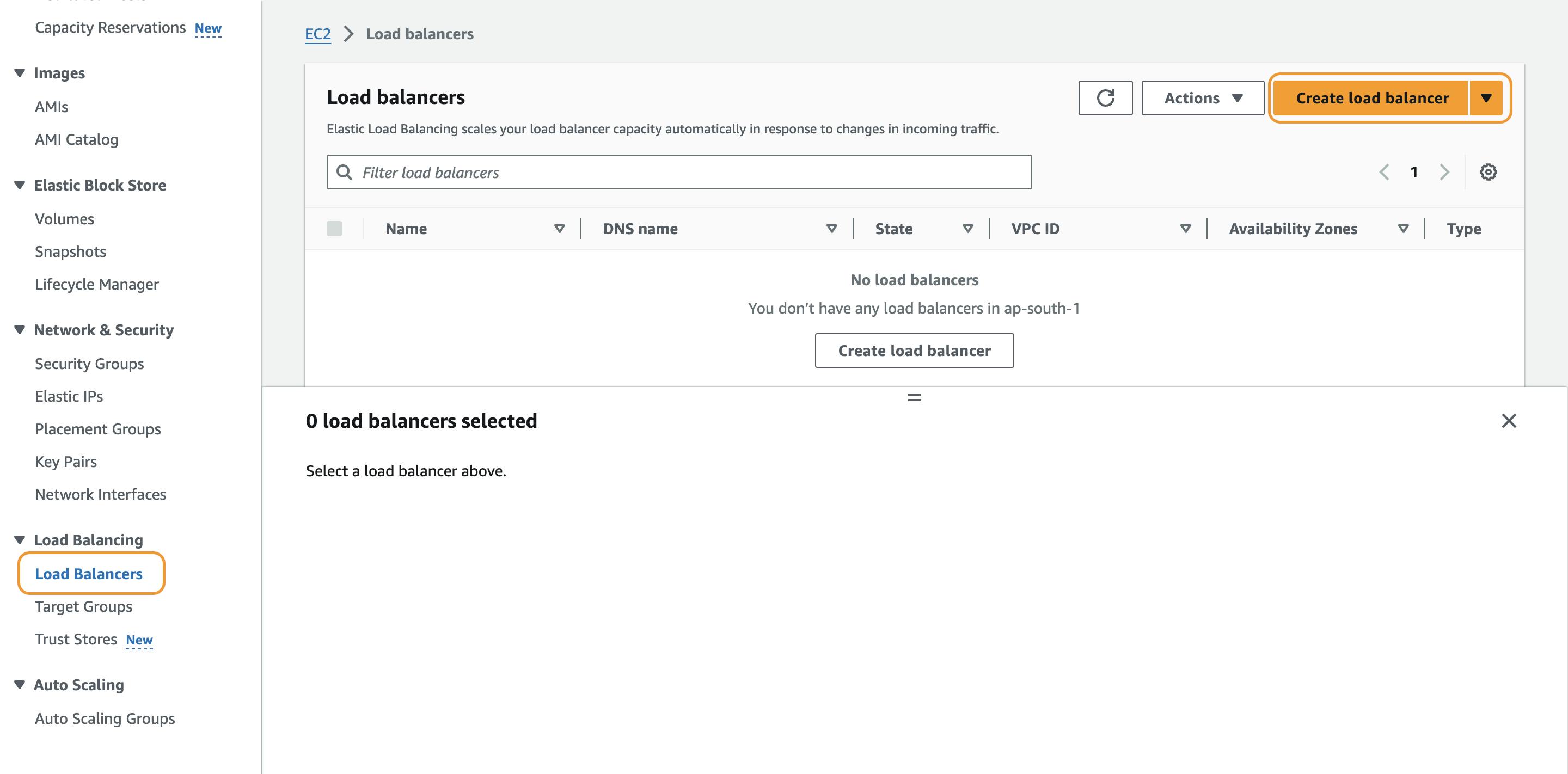
Choose "Application Load Balancer" and configure the settings, including listener configurations.
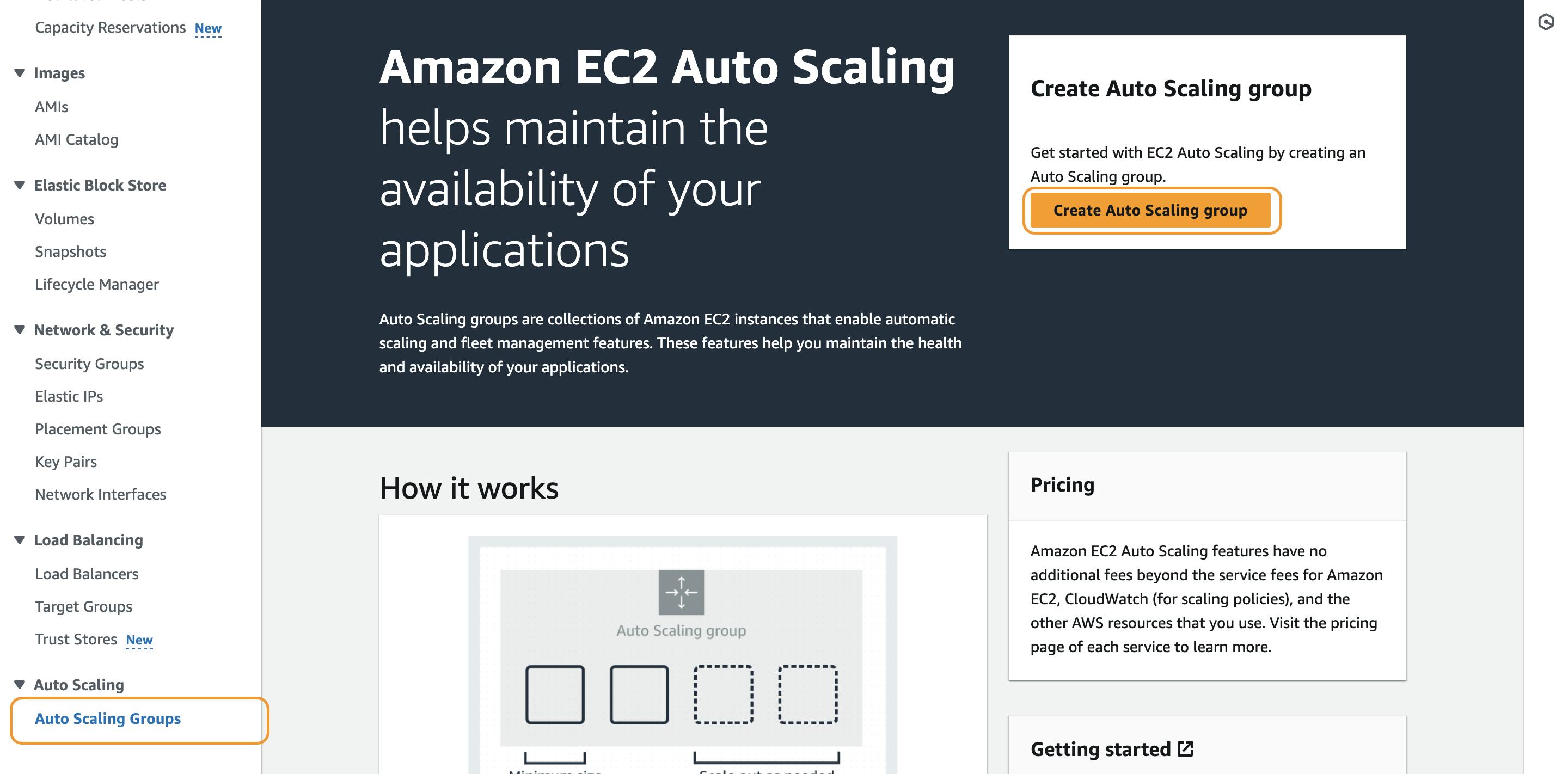
Follow the below Steps:
configure the setting and create the auto scaling group.
select the VPC you want
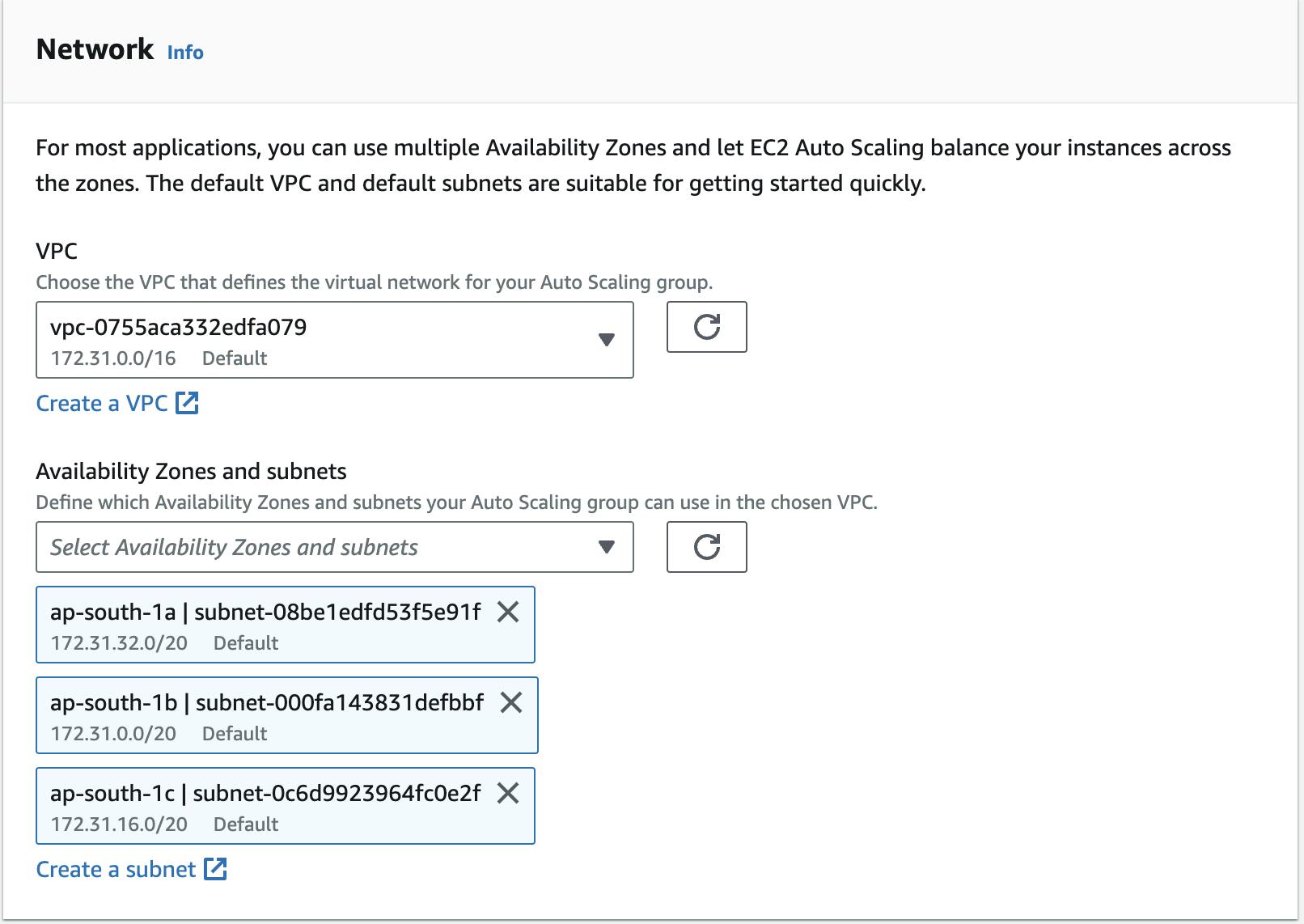
Configure scaling policies, desired capacity, and other parameters.


Securing Your Infrastructure with WAF:
Step 4 - Configuring WAF WebACL:
In the AWS WAF console, go to WebACLs and click "Create WebACL."
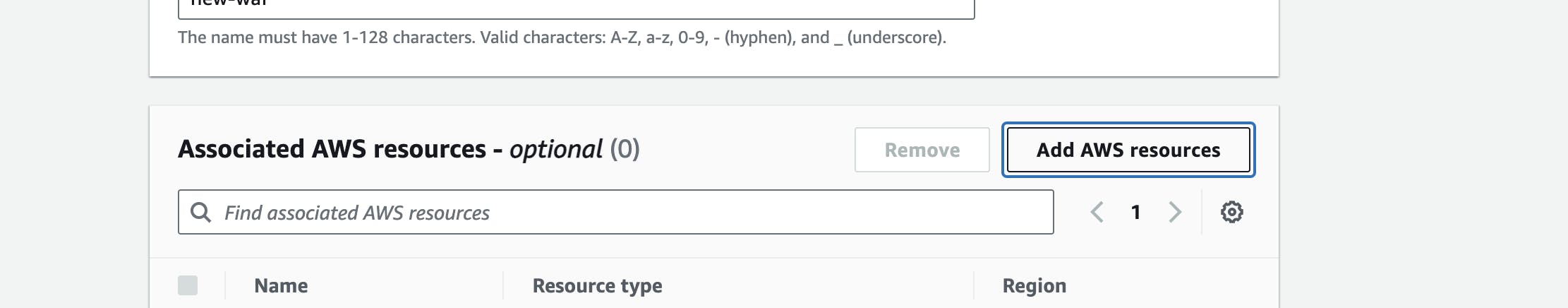
Now Click on Add AWS resources and select the load balancer we created earlier
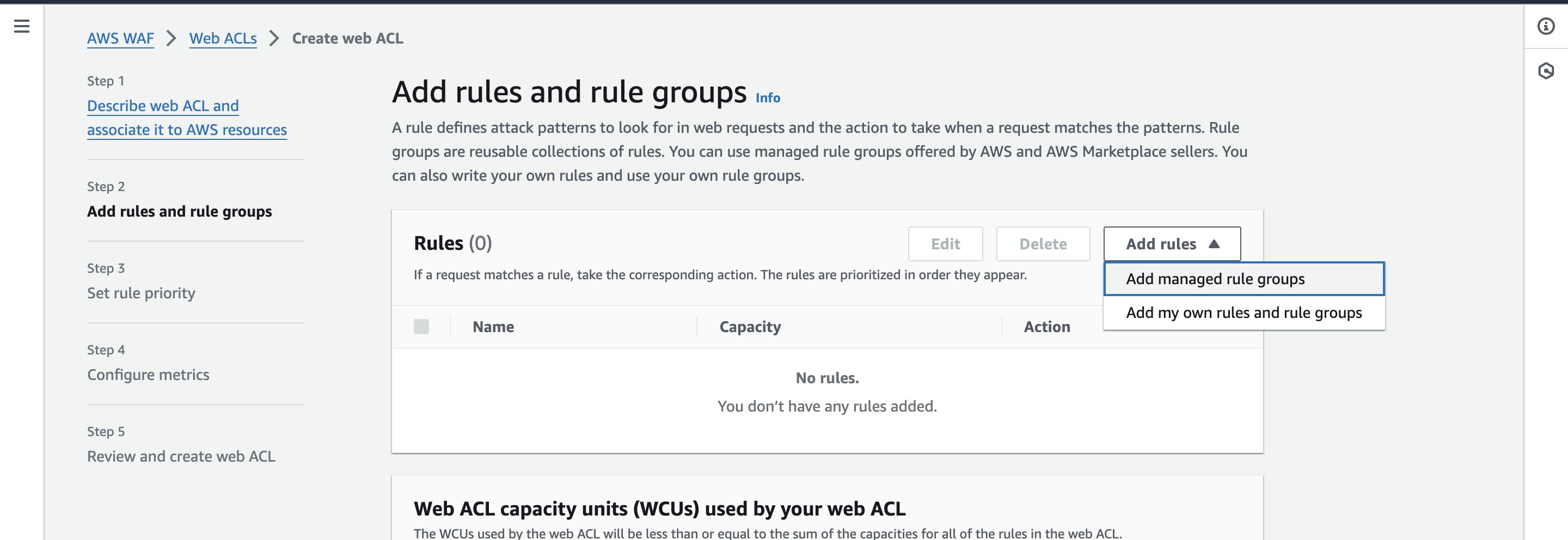
Define conditions for your WebACL, specifying rules to allow or block requests.
Associate the WebACL with your Application Load Balancer.
By configuring a WAF WebACL, you add an additional layer of protection to your applications, safeguarding them against various cyber threats.
Conclusion
If you have any questions, need clarifications, or want to discuss anything related to cloud technologies, feel free to reach out to me on LinkedIn. Connect with me at Shubham Gour, and I'll be more than happy to assist you. 😊